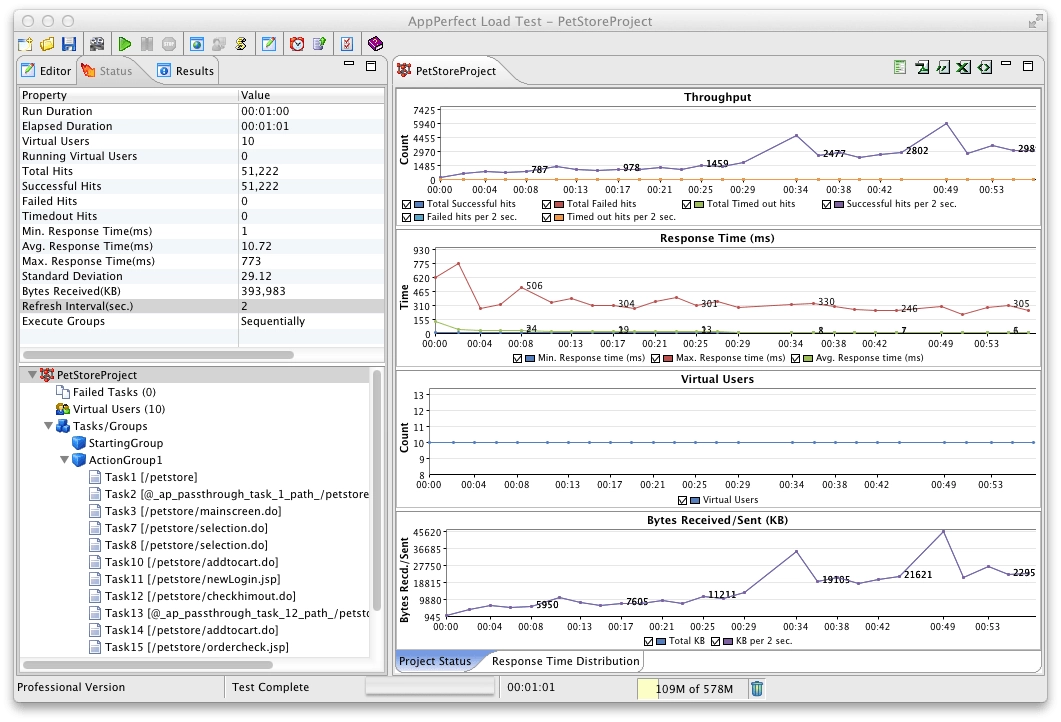
 Load / Stress Testing
Load / Stress Testing
Realistic simulation of peak loads before go live.
We are cyber security engineers with expertise in software performance testing and we can help you identify performance issues before your customers do.
Stress Testing Service
Stress Testing can help verify the stability and reliability of a system.
Our research led approach differentiates us from common penetration testing approaches with an objective to determine a systems robustness and error handling under extremely heavy load conditions.
Our approach includes stress testing well beyond the normal expected operating point and to evaluate how a system works under extreme conditions, to ensure that a system will not crash under heavy load situations.
Under Stress Testing (also known as Endurance Testing) as per our approach, the Application Under Testing (AUT) is stressed for a short period of time to know its withstanding capacity. Our core focus is to determine the limit, at which the system or software or hardware breaks and whether the system demonstrates effective error management under extreme conditions.
Depending on the scale that we will need to run, we can create a master-slave architecture on the AWS and do the same type of tests, distributed, built on-demand, depending on the amount of traffic that we will do the simulation with.
Services that we have conducted so far, are related to Application Layer simulations (simulation normal user different actions with different thresholds of users, different times, spikes etc.) or Volumetric attacks where we simulated with a specific nr of users/visitors decided together with the client (calculating the bandwidth that we will want to achieve).
Type of tests, all of them in conjunction with different agents operating under a master:
– Slowloris attack (different methods and headers)
– HTTP POST/GET flood
– UDP flood
– SSL/TLS renegotiation technique
Focus during Stress Testing
– To accommodate such abnormal traffic spikes.
– To check whether the system works under abnormal conditions.
– Displaying appropriate error message when the system is under stress.
– System failure under extreme conditions.
– It is better to be prepared for extreme conditions by executing Stress Testing.
Goal of Stress Testing
When Stress Testing our goal is to analyse the behaviour of the system after a failure.
For stress testing to be successful, the tested system should display an appropriate error message while it is under extreme conditions.
When undertaking Stress Testing, sometimes, massive data sets are used which may get lost during Stress Testing. Our Stress Testers check parameters to ensure they don’t lose security-related data while under stress testing.
The main purpose of stress testing is to check how fast system recovers after failure.
Load Testing Vs Stress Testing
|
Load Testing |
|
Stress Testing |
|
|
Load Testing is designed to test the system behaviour under normal workload conditions, and it is just testing or simulating with the actual workload.
Load testing does not break the system. |
|
Stress testing is to test the system behaviour under extreme conditions and is carried out till the system failure.
Stress testing tries to break the system by testing with overwhelming data or resources. |
|
Methodologies and Best Practices
We follow different approach’s while performing Stress testing depending on the goal(s) to be achieved as set by the client at commencement of project.
Performance Modelling and performance testing on scaled environments are very useful and provide very good analysis of potential performance issues. However, network testing to actual volumes provides the highest level of risk mitigation when verifying the capacity and performance requirements of a system.
The most reliable and risk adverse approach is to load test to the most realistic concurrent volumes.
Distributed Stress Testing
In this image the server can connect with 2 clients (Client 1 and Client 2), but it cannot send or receive a signal from Client 3 & 4.
In distributed client-server systems, testing is done across all clients from the server.
The role of server under stress testing is to distribute a set of stress tests to all stress clients and track on the status of the client. After the client contacts the server, the server adds the name of the client and starts sending data for testing.
Meanwhile, client machines send a signal or heartbeat that it is connected with the server.
If the server does not receive any signal from the client machine, it needs to be investigated further and debugged.
Application Stress Testing
During Application Stress Testing we concentrate on finding defects related to data locking and blocking, network issues and performance bottlenecks in an application.
Transactional Stress Testing
Transactional Stress Testing is focused on stress testing on one or more transactions between two or more applications. It is used for fine-tuning & optimizing the system.
Systemic Stress Testing
Systemic Stress Testing is deployed for integrated stress testing which can be tested across multiple systems running on the same server. It is used to find defects where one application data blocks another application.
Exploratory Stress Testing
Exploratory Stress Testing is a scenario used to test the system with unusual parameters or conditions that are unlikely to occur in a real scenario. Exploratory Stress Testing is used to find defects in unexpected scenarios such as:
– A large number of users logged at the same time
– If a virus scanner started in all machines simultaneously
– If Database has gone offline when it is accessed from a website
– When a large volume of data is inserted to the database simultaneously
Load Testing Networks
Where a system can support testing to actual volumes we have a performance testing service to meet your requirements.
This service also offers a comprehensive security validation by testing your system while it is experiencing peak load and while some of that load is attacking traffic.
Our Stress Testing Methodology
Our Stress Testing process follows a 6-step plan:
Planning the Stress Test – In this step we gather system data, analyse the system and define the stress test goals
Create Automation Scripts – In this step we create the Stress Test automation scripts and generate the test data for the stress scenarios.
Script Execution – In this step we run the Stress Test automation scripts and store the stress results.
Results Analysis – In this step we analyse the Stress Test results and identify bottlenecks.
Tweaking and Optimization – In this step we fine-tune the system, change configurations and optimize code with the goal of meeting desired benchmarks.
Rerun the entire cycle – In this step we run the entire cycle to determine that changes made have produced desired results. It is not unusual to have to 3 to 4 cycles of the Stress Test process to achieve the performance goals
Tools we use for Stress Testing
LoadRunner
LoadRunner from HP is a widely-used Load Testing tool. Load Test Results shaped by LoadRunner are considered as a benchmark.
Jmeter
Jmeter is an Open-Source testing tool. Jmeter is a pure Java application for stress and Performance Testing. Jmeter is intended to cover types of tests like load, functional, stress, etc. It needs JDK 5 or higher to function.
Stress Tester
Stress Tester provides extensive analysis of web application performance.
Neo load
Neo load is a popular tool available in the market to test the web and Mobile applications. Neo load can simulate thousands of users in order to evaluate the application performance under load and analyse response times. Neo load also supports Cloud-integrated-performance, load and stress testing.
Metrics for Stress Testing
Metrics help in evaluate a system’s performance and are generally studied at the end of Stress Test.
Metrics commonly deployed by XCELIT for Stress Testing are:
Measuring Scalability & Performance
Pages per Second – Measures how many pages have been requested per second. –
Throughput – Basic Metric – Response data size per second.
Rounds – Number of times test scenarios have been planned versus the number of times a client has executed
Application Response
Hit time – Average time to retrieve an image or a page.
Time to the first byte – Time is taken to return the first byte of data or information.
Page Time – Time is taken to retrieve all the information in a page.
Failures
Failed Connections – Number of failed connections refused by the client (weak signal).
Failed Rounds – Number of rounds it that failed. (Rounds – Number of times test scenarios have been planned versus the number of times a client has executed).
Failed Hits – Number of failed attempts by the system (broken links or unseen images).
Summary of our Stress Testing Service
Our Stress Testing service provides a comprehensive concurrent user simulation of user and system traffic. Stress Testing can be conducted while concurrently generating threats and attacking traffic at high loads. We can scale user behaviour to enormous maximum volumes based on your requirements. This service allows us to measure the transaction response time and service availability of your end users during periods of the highest levels of traffic.
Load testing under real world loads allows us to isolate and resolve problems before your customer encounters them. Our load testing service includes all the hardware and software to generate unlimited user loads in a realistic controlled load test.




















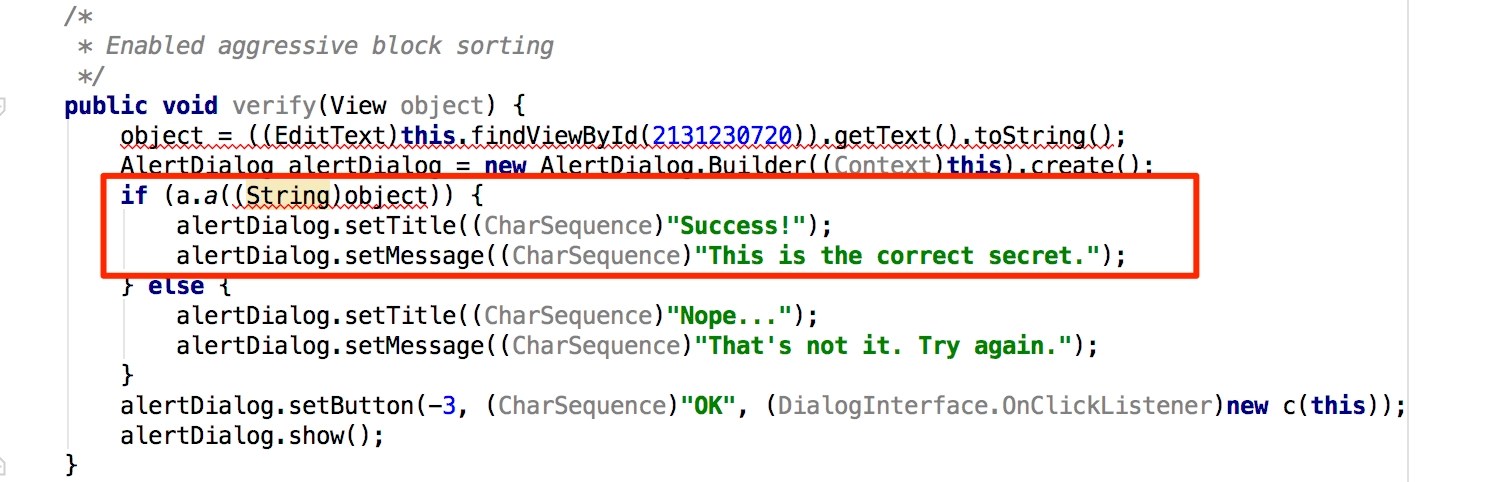
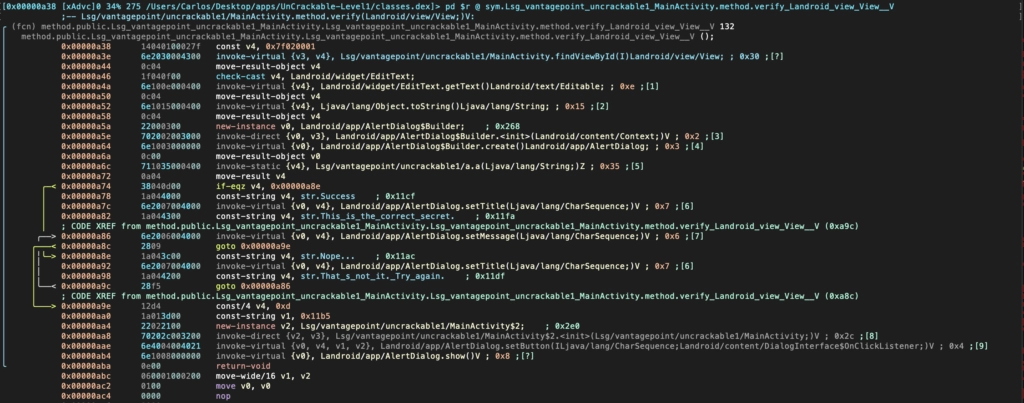
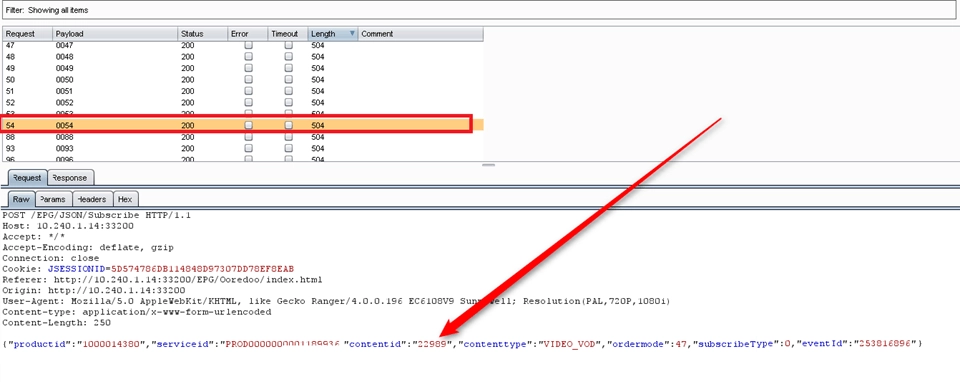
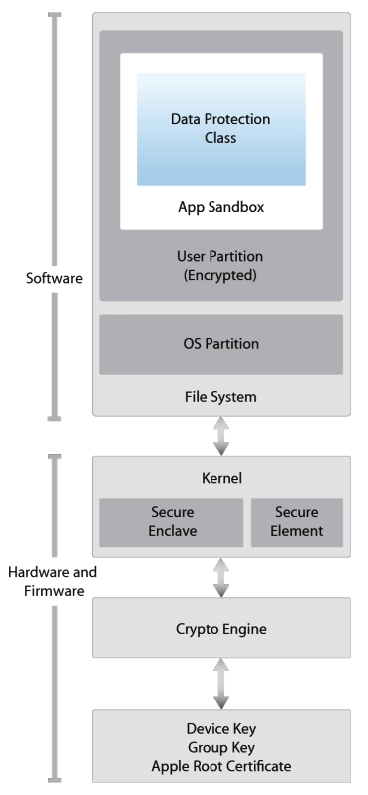
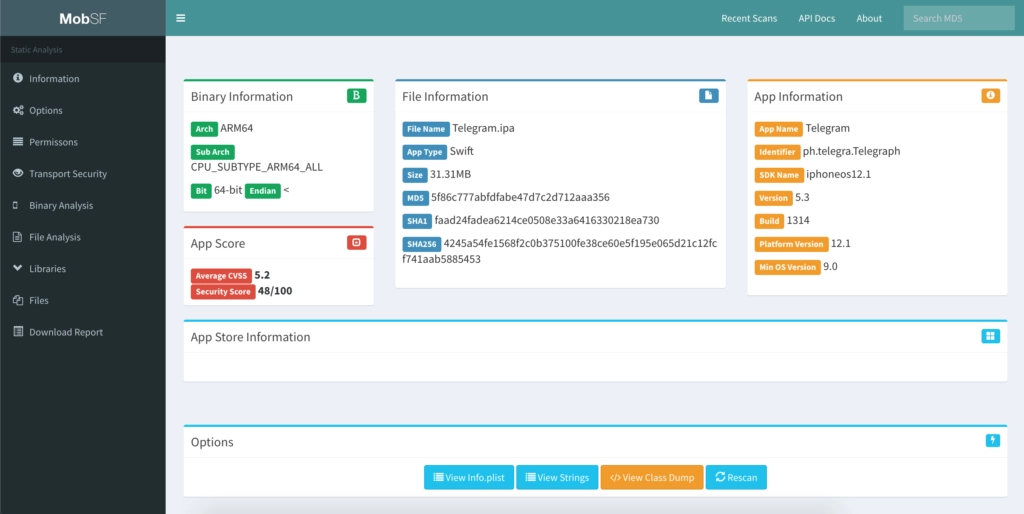 Search for sensitive information disclosures & decompile to source code.
Search for sensitive information disclosures & decompile to source code.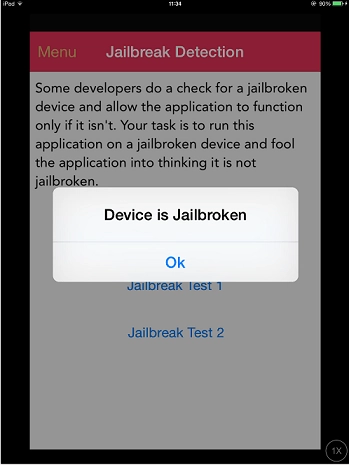
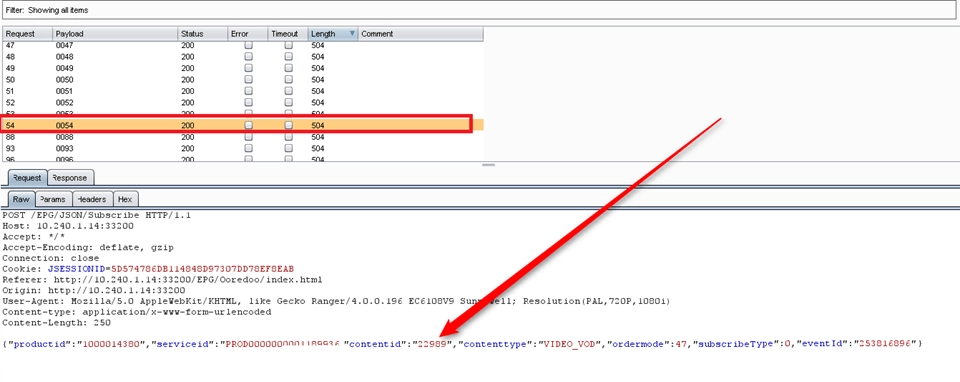
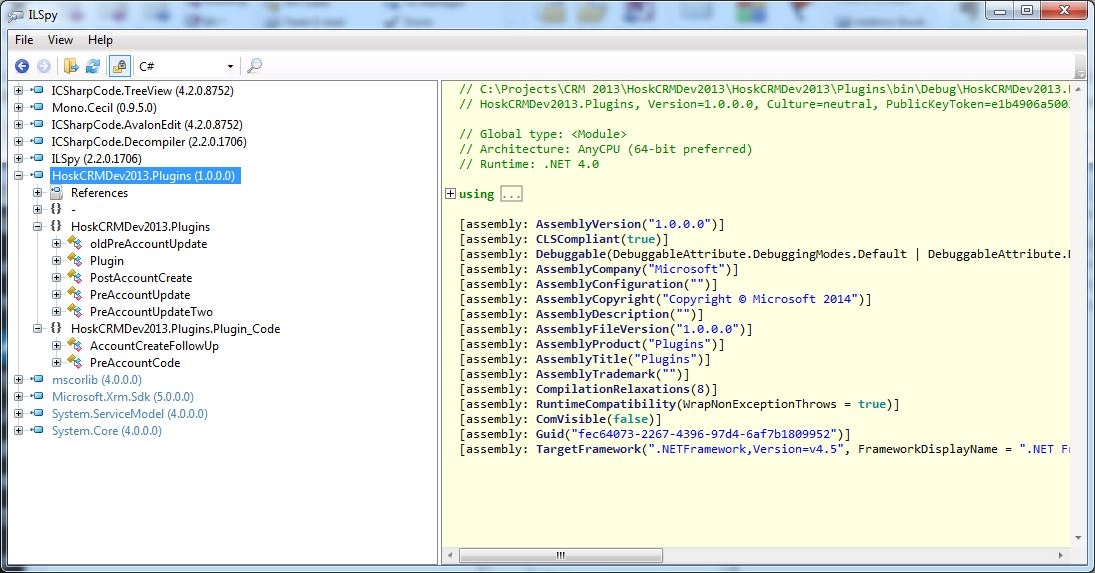
 .NET, C/C++, Microsoft Silverlight, Java applets and other types of desktop applications require thorough testing in order to be secured due to their size and the complexity of their technologies.
.NET, C/C++, Microsoft Silverlight, Java applets and other types of desktop applications require thorough testing in order to be secured due to their size and the complexity of their technologies.





 Server side Testing
Server side Testing
 Load / Stress Testing
Load / Stress Testing