Going Beyond Confidentiality, Integrity and Availability
We Provide the
People, Processes, Technology and Knowhow
To Protect Your
Businesses, Customers, Partnerships and Investors
So, you can
Be Focused on the Business of Your Business

Real Service, Real Response
Genuine AlienVault MDR Cyber Security Service:
– Conducting investigations
– Data Ingestion Minimisation to save cost
– Eyes on Glass Security Operations Centres
– Fast Investigation and Response
– Full set-up assistance
– Isolating devices
– Managing alerts
– Security Automation and Orchestration Response (SOAR)
– Setup and Execution of Automated Playbooks
– Manual prevention of persistence and lateral movement
– Manual prevention of sophisticated attacks
– Proactive 24/7 response
– Setup of customised dashboards for data insights
– Terminating malicious processes

When AlienVault MDR Cyber Security is Best
Our AlienVault MDR Cyber Security service combines our Technology, People, Processes and Knowhow with the SIEM and SOAR capabilities of AlienVault and the world’s largest threat intelligence pool.
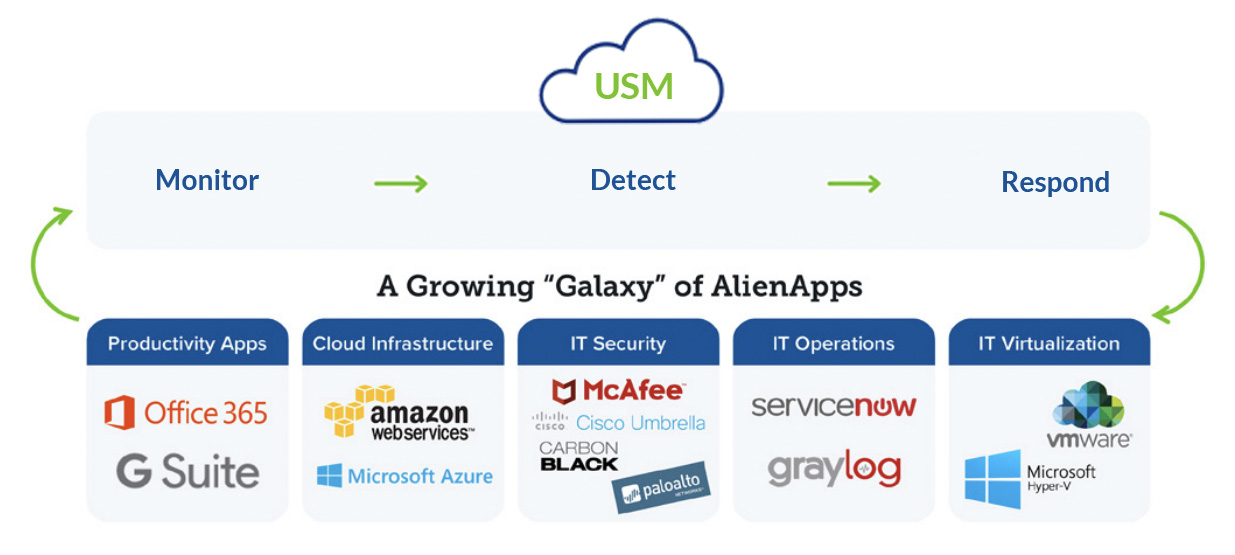
AlienVault can detect threats, On Premise, and in the Cloud (Azure, AWS and Google), at Endpoints and from hundreds of SaaS applications. Combined with the ability to ingest data from all leading security vendors our MDR Service is extremely flexible making our MDR service appropriate where flexibility is needed.
AlienVault is best when networks use mixed cloud and multiple Cyber Security Vendors.
Managed Workloads for Fast Response
Fast Detection, Investigation and Response Matters
With controls on data under management per staff member, XCELIT ensures we can provide the kind of response times you expect from an Eyes on Glass operation

AlienVault MDR Cyber Security Service Inclusions
Essentials
Standard
Premium
Hot Storage (Real Time Event Search)
ESSENTIALS
15 Days
STANDARD
30 Days
PREMIUM
90 Days
Any event log collected by XCELIT’s AlienVault MDR Cyber Security Service is stored within compliant-ready and secure hot storage for the specified period of time (15, 30 or 90 days). The standard approach used is a write once, read many (WORM) to log storage in order to prevent log data from being modified or otherwise tampered with. Hot storage allows for faster viewing of event history in the case of forensics.
Cold Storage (AWS)
ESSENTIALS
Infinite (unlimited) Days
STANDARD
Infinite (unlimited) Days
PREMIUM
Infinite (unlimited) Days
Any event log collected by XCELIT’s AlienVault MDR Cyber Security Service is stored within compliant-ready and secure cold storage (AWS). Data is kept indefinitely in cold storage for as long as invoices continue to be paid, with download capability also available. The standard logging approach used is a write once, read many (WORM) to log storage in order to prevent log data from being modified or otherwise tampered with.
Raw logs are available at any time, for example in the case of forensics such as investigating a fraud incident within an organisation which may require log events to be investigated several years into the past.
Eyes on Glass SOC Monitoring
ESSENTIALS
12x5 (Mon-Fri)
STANDARD
24x7
PREMIUM
24x7
XCELIT’s AlienVault MDR Cyber Security Service monitors and analyses activity across the entire network including on-premise, off-premise cloud, endpoints and hundreds of common applications looking for anomalous activity that could be indicative of a security incident or compromise.
With XCELIT the effort doesn’t end with systems, XCELIT’s AlienVault MDR Cyber Security Service leverages people, processes, and technology to continuously monitor and improve your organization’s security posture while preventing, detecting, analysing, and responding to cybersecurity incidents as per your IRP Incident Response Plan.
XCELIT’s AlienVault MDR Cyber Security Service is the core of XCELIT’s piece of mind Cyber Security.
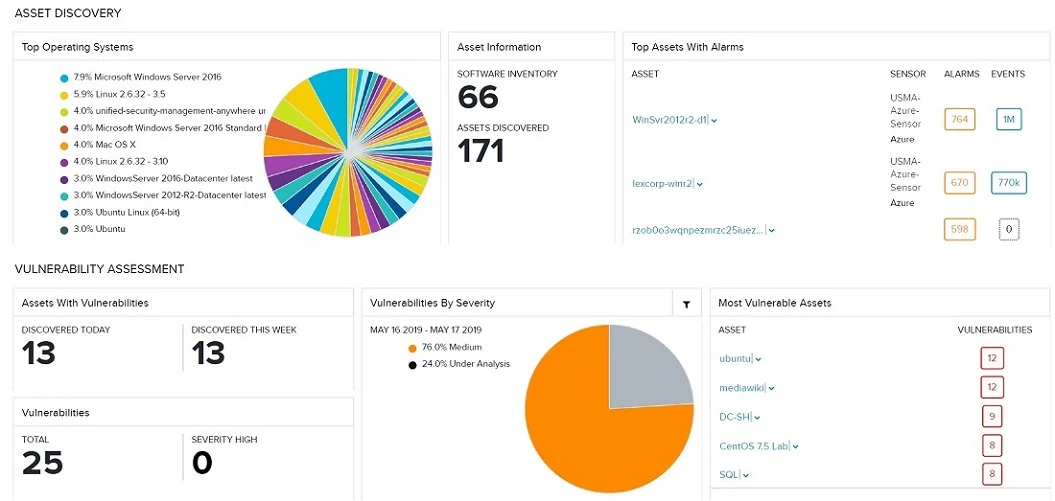
Asset Discovery & Inventory
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service uses tools to discover and inventory all the assets (servers, desktops, laptops, connected mobiles, virtual machines, containers, firewalls, switches, and printers, etc) in your network and correlate asset information with threat and vulnerability data.
Vulnerability Scanning
ESSENTIALS
STANDARD
PREMIUM
The dynamic nature of today’s cloud, on-premises, and hybrid network environments requires continuous network vulnerability scanning to defend against the evolving threat landscape. Constant application updates and changes to application and system configurations can introduce vulnerabilities and leave you susceptible to an attack, even if you are keeping your security controls up to date.
XCELIT’s AlienVault MDR Cyber Security Service vulnerability scanning identifies and creates an inventory of all the systems (servers, desktops, laptops, connected mobiles, virtual machines, containers, firewalls, switches, and printers etc) connected to a network. For each device that it identifies it also attempts to identify the operating system it runs and the software installed on it, along with other attributes such as open ports and user accounts.
After building up an inventory, the vulnerability scanner checks each item in the inventory against known vulnerabilities to see if any items are subject to any of these vulnerabilities.
Vulnerability Assessments
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service performs vulnerability assessments to define, identify, classify and prioritise vulnerabilities across your entire network so that the most critical vulnerabilities (those that a Hacker may exploit) can be taken care of with priority.
XCELIT’s AlienVault MDR Cyber Security Service performs vulnerability assessments on an ongoing basis and responds as per the Incident Response Plan (IRP) in place with our clients.
Intrusion Detection
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service employs intrusion detection software as part of XCELIT’s service offering. XCELIT’s solution includes built-in host intrusion detection (HIDS), network intrusion detection (NIDS), as well as cloud intrusion detection (CIDS) for public cloud environments including Google Cloud, AWS and Microsoft Azure, enabling you to detect threats as they emerge in your critical cloud and on-premises infrastructure.
SIEM Event Correlations
ESSENTIALS
STANDARD
PREMIUM
Security Information and Event Management (SIEM) is where software products and services combine security information management and security event management. Providing real-time analysis of security alerts generated by applications and network hardware.
XCELIT’s AlienVault MDR Cyber Security Service employs SIEM Event Correlations. SIEM event correlations are an essential part of any SIEM solution. SIEM event correlation aggregates and analyses log data from across your network applications, systems, and devices, making it possible to discover security threats and malicious patterns of behaviours that otherwise go unnoticed and can lead to compromise or data loss.
Generated data for SIEM event correlations can be overwhelming. XCELIT’s systems take available information and filters out noise to generate actionable intelligence related to which events could cause a security breach, allowing targeted response.
Incident Response
ESSENTIALS
STANDARD
PREMIUM
XCELIT, with our clients, develop a Full Incident Response plan which is followed by our AlienVault MDR Cyber Security Service, providing you with confidence that a level of response is regularly employed on your behalf.
Incident Response is best driven by an incident response plan. If you do not yet have an Incident Response Plan, a XCELIT representative can assist with developing one with or for you. If you already have an Incident Response Plan, XCELIT’s AlienVault MDR Cyber Security Service can augment into your existing plan.
Endpoint Detection & Response
ESSENTIALS
STANDARD
PREMIUM
Endpoint detection and response (EDR), also known as endpoint threat detection and response (ETDR), is an integrated endpoint security solution that combines real-time continuous monitoring and collection of endpoint data with rules-based automated response and analysis capabilities.
Endpoints include not only desktops and servers, but laptops, tablets, smartphones and internet of things (IoT) devices.
Increasingly, endpoints represent one of the top areas of security risk for organizations and as a result, EDR is becoming increasingly important. Cyber criminals are increasingly designing their attacks to evade traditional endpoint prevention and protection tools, in response XCELIT’s AlienVault MDR Cyber Security Service as part of our services seek evidence of attacks that might not trigger traditional prevention rules.
While many security teams recognize the need for advanced threat detection for endpoints, most do not have the resources to manage a standalone EDR solution.
Endpoint detection and response solutions, such as that employed by XCELIT’s AlienVault MDR Cyber Security Service record system activities and events taking place on endpoints and provide XCELIT’s AlienVault MDR Cyber Security Service team with the advanced analytics they need to uncover incidents that would otherwise remain invisible. Commonly also known as detecting and investigating suspicious activities on hosts and endpoints.
XCELIT’s AlienVault MDR Cyber Security Service platform centralizes and automates threat hunting on endpoints across your cloud and on-premises environments, so we can detect and respond to threats wherever they unfold.
The ability to unify data from both cloud and on-premises endpoints allows XCELIT’s AlienVault MDR Cyber Security Service to obtain a holistic view rather than a siloed view from different systems represents one of the main advantages of XCELIT’s Endpoint Detection and Response solution.
Log Management
ESSENTIALS
STANDARD
PREMIUM
Raw logs are an invaluable asset for forensic analysis and compliance mandates. XCELIT’s AlienVault MDR Cyber Security Service can review logs to find details about specific incidents, search the logs for instances using a specific IP address, or analyse the patterns of multiple attacks.
Compliance Management
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security service combines the essential security technologies needed to demonstrate compliance against today’s most challenging regulatory standards such as PCI, HIPPA, ISO 27001 and NIST CSF, or to meet compliance to any internal IT system requirements.
Let XCELIT know what you need and XCELIT will provide you with our best available standardised reporting, or generate custom reports at an additional service fee if not readily available.
Email Alerts
ESSENTIALS
STANDARD
PREMIUM
For certain important events, you may want a notification to be sent to you or your team to inform them immediately. XCELIT’s AlienVault MDR Cyber Security team will set these up for you. If you do not have any specific requirements, XCELIT will recommend some and you may opt in if you choose.
File Integrity Monitoring
ESSENTIALS
STANDARD
PREMIUM
File Integrity Monitoring (FIM) refers to an IT security process and technology that tests and checks operating system (OS), database, and application software files to determine whether or not they have been tampered with or corrupted.
The process employed by XCELIT’s AlienVault MDR Cyber Security Service is called syscheck. The syscheck process scans the host at user-defined intervals and stores checksums of watched files. A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. The system then generates an event when a checksum changes.
XCELIT’s AlienVault MDR Cyber Security Service system can also configure Windows systems so that host-based intrusion detection system (HIDS) agents forward object access audit events to the AlienVault MDR Cyber Security Service.
Audit events provide more information regarding the operations affecting file and folder objects, such as who performed specific actions or operations on an object.
System & User Behaviour Monitoring
ESSENTIALS
STANDARD
PREMIUM
User behaviour monitoring is a new approach to insider threat prevention and detection. XCELIT’s system determines what is normal use and then monitors for abnormal use.
Implementing user behaviour monitoring is obligatory to comply with a lot of industry standards (e.g. NIST, HIPAA, PCI DSS, etc.).
Context is critical when evaluating system and network behaviour. For example, an abundance of Skype traffic in the network used by your inside sales team is probably a normal part of operations. However, if the database server that houses your customer list suddenly shows a burst of Skype traffic something is likely wrong.
Therefore, as soon as your XCELIT AlienVault MDR Cyber Security Service solution is implemented, behavioural monitoring functionality starts gathering data to help you understand normal system and network activity. XCELIT’s AlienVault MDR Cyber Security Service solution provides network behavioural analysis with service availability monitoring to create a full picture of system, service, and network anomalies.
Monthly Reporting & Dashboard View
ESSENTIALS
STANDARD
PREMIUM
XCELIT can manage your reporting and dashboard needs.
Dashboards – Your internal IT team or curious nominated staff can access dashboards.
Reporting – XCELIT’s reports are designed so they are easy to understand, not just for IT professionals.
Reports can be delivered to you monthly, including PCI, NIST CSF, HIPAA, and ISO 27001 compliance reports, alarm reports, asset reports and create event reports.
Integrating Ticketing & Alerting
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service can integrate with Service Now, Jira, Slack, Datadog. Jira being the most common ticketing and alerting system.
Orchestration with Security Tools
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service systems allow for orchestration and automation of threat detection and response across an ever-growing ecosystem of third-party security tools and IT applications, including Palo Alto Networks, Cisco Umbrella, Carbon Black, and many other Apps.
Automated Incident Response & Forensics
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service employs Automated Incident Response & Forensics with the intention of saving you money and reducing the cost of Cyber Security.
Automation expedites typical responses and repetitive tasks so little to no human intervention is required to detect and respond to security threats and incidents.
Digital forensics helps IT professionals (SOC Engineers and SOC Analysts) identify instances of cybercrime like malware and hacking.
By automating incident response, XCELIT’s AlienVault MDR Cyber Security Service team can improve performance and save time, essentially giving you more for less, saving you money.
An example of automation is whereby as soon as ransomware is detected and an alarm is raised your system automatically responds by isolating the infected machines, allowing for a controlled response, rather than a mad dash to your servers or systems and frantically unplugging infrastructure.
With the right automated incident response, XCELIT and your IT security team combined can stay in control of their incident response (IR) activities and respond to threats and intrusions swiftly and effectively, with less manual work—no wire-ripping required.
Dark Web Monitoring
ESSENTIALS
STANDARD
PREMIUM
Dark Web Monitoring employed by XCELIT’s AlienVault MDR Cyber Security Service leverages SpyCloud technology to monitor the dark web to discover if your users’ credentials, such as email addresses, usernames, and passwords, have been stolen.
If detected, XCELIT’s AlienVault MDR Cyber Security Service alerts you so that you can respond swiftly to the compromise, such as requesting users to change details and cancel credit cards, ahead of a breach.
While momentarily inconvenient, your customers will thank you and the efforts of another hack will be thwarted.
Support for High Data Volumes
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security system can manage your data needs, you need not be concerned about our capacity to cope. Importantly however, XCELIT’s implementation plan is structured to ensure you get maximum bang for your data scanning buck by avoiding white noise data.
Supports PCI Log Storage Requirements
ESSENTIALS
STANDARD
PREMIUM
Payment Card Industry Data Security Standard (PCI DSS) is a security standard used to ensure the safe and secure transfer of credit card data.
PCI DSS compliance software is a must-have for any organization that handles credit card data or other types of payment card data. Failure to comply can result in PCI DSS penalties and fines imposed daily, and a data breach resulting from non-compliance could cost millions in settlements, legal fees, and loss of reputation.
XCELIT’s AlienVault MDR Cyber Security Service solution provides everything you need to get ready for your next PCI DSS audit in one affordable, easy-to-use solution. XCELIT’s AlienVault MDR Cyber Security Service solution combines the essential security technologies you need to demonstrate compliance, including asset discovery, vulnerability assessment, log management, file integrity monitoring, and others. It also provides predefined compliance reports out of the box and automatic threat intelligence updates, helping you to stay in compliance with continuous security monitoring.
Advanced Threat Intelligence
ESSENTIALS
STANDARD
PREMIUM
XCELIT’s AlienVault MDR Cyber Security Service systems provide up to date information related to sophisticated malware or hacking-based attacks targeting sensitive data. Where possible, XCELIT integrates with security tools to automate the response within your environment. With automated feeds of threat intelligence, combined with our AlienVault MDR Cyber Security Service team of analysts XCELIT provides proactive threat hunting, enhanced abilities to prevent incidents before they occur, and respond to events in real time.
Included Sensors
ESSENTIALS
As many as needed
STANDARD
As many as needed
PREMIUM
As many as needed
Lightweight sensors and agents are the only components deployed in your environment.
Sensors employed by XCELIT provide deep security visibility into both your cloud and on-premises environments.
XCELIT’s AlienVault MDR Cyber Security Service virtual sensors run on VMware and Microsoft Hyper-V to monitor your on-premises physical and virtual IT infrastructure. In the cloud, lightweight cloud sensors natively monitor Google Cloud, Amazon Web Services and Microsoft Azure Cloud.
Each sensor is purpose-built to fully leverage the native data collection methods of each environment: AWS, Azure, and on-premises physical and virtual infrastructure deployed on Hyper-V or VMware. Deployed agents collect data from your Windows and Linux endpoints.
Deployed sensors conduct scans, monitor packets on the networks, and collect logs from assets, the host hypervisor, and cloud environments. Collected information is stored in XCELIT’s AlienVault MDR Cyber Security Service secure cloud and used by XCELIT’s AlienVault MDR Cyber Security Service in providing Cyber Security services.
The deployment of sensors by XCELIT allows centralized security monitoring of your cloud, on-premises, and hybrid IT environments, including your endpoints and cloud apps like Office 365 and G Suite amongst others.
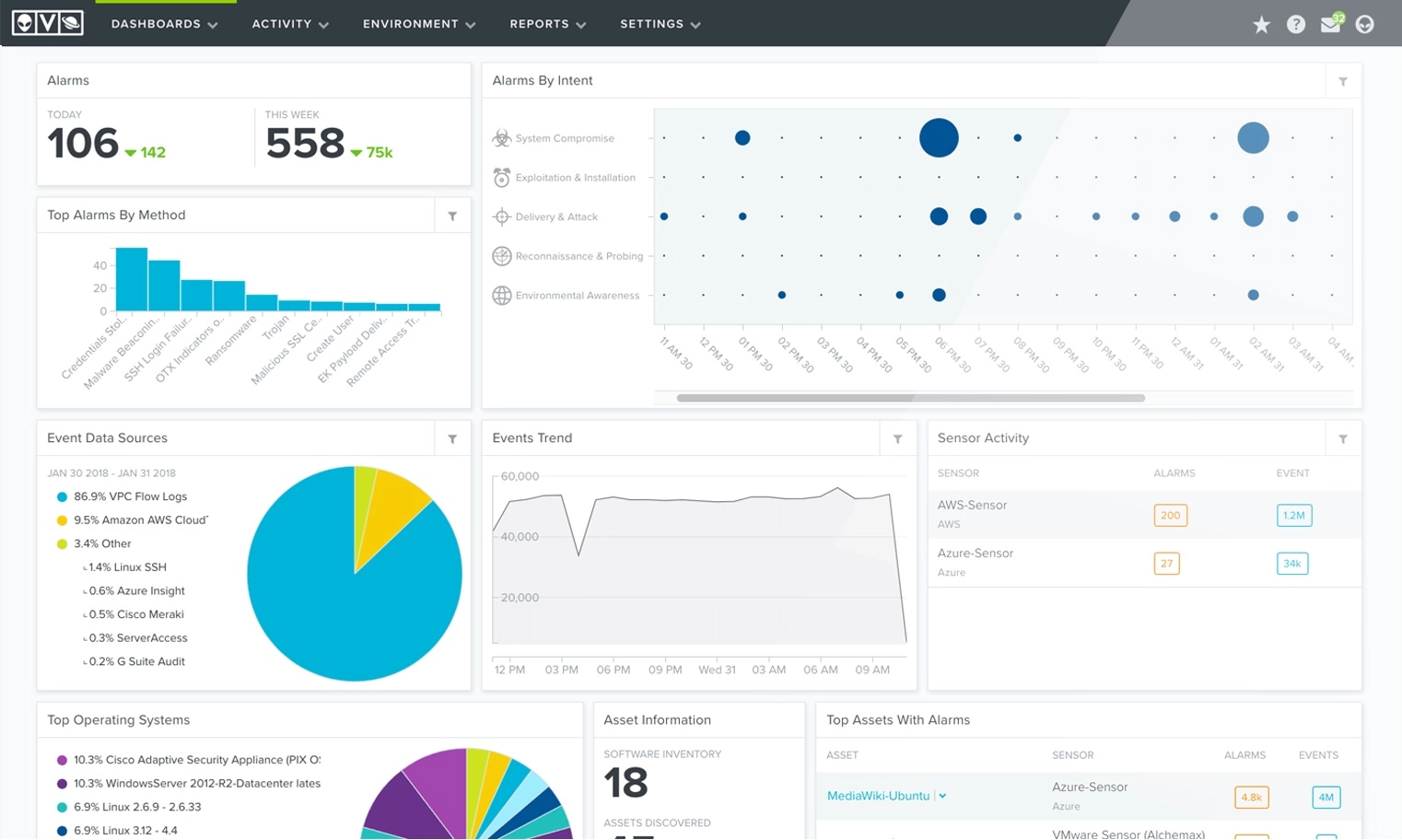
Custom Dashboards
XCELIT has developed and applies a number of custom dashboards within AlienVault to provide our SOC teams with greater insights into client environments than would be achieved from native AlienVault rules/reports.
Our proprietary customised dashboards allow us to combine data from disparate sources to create rich data insights. You gain from our experience with AlienVault as we use insights to check correlated security events, availability, performance, usage, and overall health of the underlying components of your network.
The boards asking about security, we have a dashboard for that.
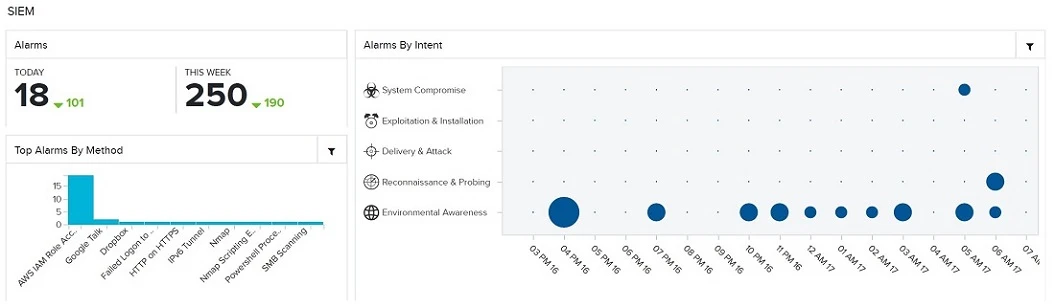
Alarm Monitoring and Investigation
XCELIT’s SOC’s team’s continuously monitor events and alarms within AlienVault and associated services for potential security incidents or potential risk exposure.
Alarms, combined with Threat Hunting activity, are investigated and a determinization is made whether a security incident or potential risk requires the creation of an investigation and customer notification.
If no Investigation is required, the Alarm is closed.
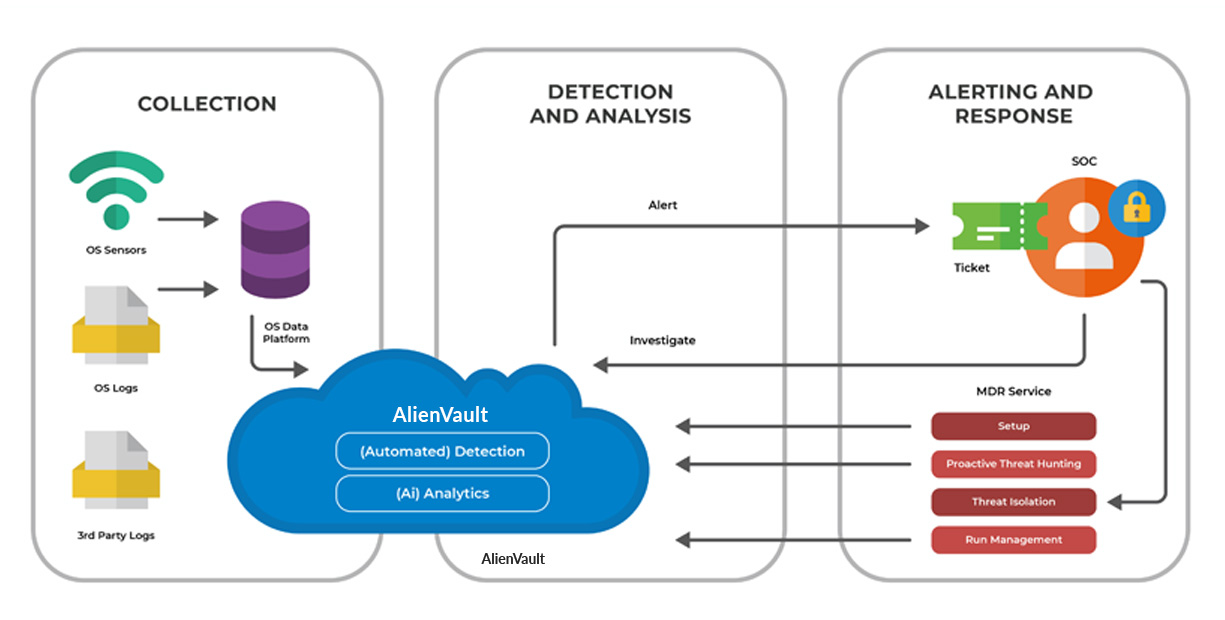
Eyes on Glass
Eyes on Glass means that our Security Operations Centre’s have people in attendance 24/7 and not just systems logging data 24/7
Via 3 Security Operations Centre’s our operations follow the Sun, allowing us to have the best, highly engaged, professional talent, on task when they are needed.

Data Sovereignty
AlienVault stores logs at your nominated AWS location(s), ensuring all data sovereignty requirements can be met.
When managing AlienVault MDR for clients, XCELIT’s 24/7 Eyes on Glass SOC teams interact with AlienVault in the same way you read internet sites online.
Which means, our interactions with AlienVault have no impact on your businesses data sovereignty.
Meaningful Monthly Reporting
Meaningful Monthly Reporting is provided to nominated recipients
Our Meaningful Monthly Reports are not just for the technical team, but are equally as helpful to executive management and board members
Message Us
10 Key Features of XCELIT's MDR Cyber Security Solution
Technology Stack
XCELIT deploys systems that combine essential security capabilities needed for effective MDR Cyber Security from a single operating system, visible from a single pane of glass.
Key features of XCELIT’ solution include asset discovery, vulnerability assessment, network intrusion detection (NIDS), endpoint detection and response (EDR), and SIEM event correlation and log management. Combined, XCELIT’s features and staff capabilities combine to provide advanced threat detection and response.
Cloud Security Monitoring
XCELIT’s MDR Cyber Security solution provides cloud security monitoring for IaaS (AWS®, Azure) and SaaS environments (Office 365, G Suite™, Okta, and Box), using APIs to continuously collect data from those environments. Backed up by extensive threat intelligence to address advanced threats before they become problematic for your business.
Alarm monitoring and validation
XCELIT’s SOC operates 24/7 to provide proactive alarm monitoring. XCELIT’s Security Analysts review every alarm, removing noise, non-actionable alarms and false positives, so focus can be applied to actual threats.
XCELIT’s analysts perform in-depth incident investigations to provide responders, as determined by the Incident Response Plan with timely, effective recommendations for containment of threats and remediation actions to ensure safe systems operations.
Incident Response
XCELIT augments with your team by undertaking in-depth, auditable trail, investigations into actionable alarms, escalating based on the Incident Response Plan to respond quickly and effectively to any identified security incident.
An auditable trail of threat intelligence, related alarms and events, conclusions, relevant files and response recommendations provides you with a consolidated view of the incident.
Backed up by XCELIT’s 24/7 SOC, XCELIT’s team are available to provide support. XCELIT however goes beyond the standard MDR Cyber Security solution and can even undertake incident response as determined by your Incident Response Plan using XCELIT’s built in security orchestration and automation capabilities.
Orchestration and Automation
XCELIT’s MDR Cyber Security solution deploys powerful security orchestration and automation capabilities to drive incident investigation and response reducing time to response reducing exposure to potential threats.
XCELIT’s Unified Security Management system includes over 300 app integrations with widely used IT, security, and business productivity tools including Box, Cisco Umbrella™, and Palo Alto Networks®. XCELIT’s Unified Security Management system, app integrations and deployed technology allows automated incident response actions towards networks, devices and other integrated security controls for significantly improved response times, minimising threats and maximising productivity.
Transparency and Availability
XCELIT’s MDR Cyber Security solution is entirely transparent. Our customers have access to the same web based portal as our SOC analysts. If needed our SOC analysts are also available via phone, email and slack.
XCELIT is primarily driven to provide a premium MDR Cyber Security solution, as such, XCELIT sets stringent SLA’s starting at 5min for a Category 1, Critical Issue.
XCELIT’s analysts set monthly meetings with clients to:
– review all investigations and incident response activities.
– review service metrics related to agreed SLAs to ensure XCELIT can maintain delivery of the client’s security program objectives.
– anticipate future needs and meet clients ongoing expectations in a dynamic environment.
Compliance Reporting Capabilities
XCELIT supports client’s (PCI, NIST CSF, HIPAA, ISO 27001) compliance reporting requirements with pre-built reporting templates.
XCELIT’s MDR Cyber Security solution includes long term log storage, including raw log retention in a highly secure environment.
If you have a compliance need, XCELIT’s commissionable platform can meet your need.
Threat Intelligence
The backbone of any MDR Cyber Security is the Threat Intelligence that the MDR Cyber Security solution is built upon.
With diverse sources including 1/3 of global internet traffic, deployed sensors combined and an Open Threat Exchange that includes 80,000 participants in 140 countries XCELIT’s Threat Intelligence is continuously updated with the best available intelligence on emerging and evolving threats.
Intelligence is useful but how intelligence is deployed is equally important. XCELIT’s partnered intelligence systems go deeper, analysing the Tools, Tactics, and Procedures (TTPs) used by threat actors so we can respond to threats as they move when low level identification such as IP’s have been exposed.
Continuously updated Threat Intelligence is used by XCELIT to perform high level automated threat detection and response, far beyond standard MDR Cyber Security solutions.
Deployment and Onboarding
XCELIT’s SOC team deploys scanners and undertakes to understand your environment, security and compliance requirements and sets out the Incident Response Plan, tuning to your requirements within 30 days. With XCELIT you can have a premium, highly effective MDR Cyber Security solution in place, fast.
XCELIT deploys MDR Cyber Security so as to minimise ingestion, saving your budget.
Scalability and Adaptability
XCELIT’s MDR Cyber Security solution is designed to be scalable, to meet your business needs now as well as into the future. You can increase your ingestion or coverage at any time, without complex contract changes.
XCELIT’s services are based on injection and data retained, you are not restrained by assets, environments or the number of employees you have. XCELIT is truly scalable and adaptable to your future needs.
Common Questions about MDR Cyber Security
What is MDR Cyber Security?
MDR Cyber Security stands for Managed Detection and Response, Cyber Security.
MDR Cyber Security is a service that is an IT cyber security service that detects intrusions, malware, and malicious activity in your network and assists in rapid response to eliminate and mitigate those threats.
Quality MDR Cyber Security services, like XCELIT’s, have a very light footprint on your network and use a combination of human analysts and technology to eliminate false positives, identify real security threats, and develop incident responses in real time.
While the average time across industries to detect a compromised asset is close to 198 days, MDR Cyber Security typically reduces that to hours, and therefore minimizes the impact of a security event.
Who needs MDR Cyber Security?
It depends on your industry as to when you may choose to obtain MDR Cyber Security, however a a guide any organisation that has ten or more staff consider MDR Cyber Security as your business will become a target for hackers or cyber criminals, more commonly known as threat actors.
The clearest need for MDR Cyber Security is among organisations that have a regulatory requirement to provide effective detection and response (healthcare, financial services, etc.), yet have no fully-staffed Security Operations Centre (SOC).
Many organisations outsource MDR Cyber Security to XCELIT to outsource recruitment and retention of talented staff, or indeed to access talent they may otherwise struggle to maintain. Cost however is a big driver, solutions such as XCELIT’s MDR Cyber Security costing much less than an equivalent in house solution would.
XCELIT is here to assist, even if you are unsure, reach out.
Is MDR Cyber Security known by other names?
Cyber Security doesn’t have to be complex, however as an industry we have made it this way.
The trick is to watch out for sales agents claiming a product is more than it is, or even calling a product something that it is not. For example, it is not uncommon for claims of a 24/7/365 SOC to be applied to services that are not eye’s on glass, which is an over reach. In these cases, SOC Services may be applied during normal shifts, but not 24/7/365, although alarm monitoring may be.
XCELIT’s MDR Cyber Security Solution is a true 24/7/365 operation with eyes on glass.
MDR Cyber Security may also be known as Managed Threat Detection and Response Cyber Security (MTDR):
Let's Talk
Contact Us